Secure Physical ID Matters – even in a virtual world

In the modern world it’s easy to characterize physical ID documents as outdated and irrelevant. But to do so would be to overlook the practical realities, and ubiquitous adoption, of these durable physical credentials.
We live in a world where the movement towards mobile and digital formats for a wide variety of identity documents – such as national IDs and driver licenses – is already underway. Indeed, the COVID-19 public health crisis has served to propel Governments to accelerate digital (mobile) ID adoption so locked-down citizens could still securely access a range of digital public and private services. Everything from registering a child’s birth to collecting pension payments, and using their digital ID to prove their ‘key worker’ status and permission to travel.
But that doesn’t mean that the physical ID document is no longer needed. Rather than simply being replaced by new digital formats, they continue to be the pre-requisite for the overall success of many schemes.
Around the globe, governments and national ID issuers continue to use physical ID documents and cards for a variety of applications and services. Portable, easy to present and validate by authorities – independent of the availability of connectivity or mobile network coverage – they continue to offer the ideal solution for citizens who can’t or won’t carry a smartphone or live in locations where mobile coverage is limited.
Many countries are upgrading their national documents and issuing convenient and secure ID documents such as mobile drivers licenses or issuing electronic ID (eID) documents that contain an integrated electronic chip capable of storing additional identification data (such as biometrics) or information relevant to the carrier. Indeed, today, more than 120 countries rely on the use of e-passports at their borders.
Clearly, physical and digital ID is becoming increasingly conjoined and for the near future both physical and digital credentials will need to co-exist.
To support governments and national authorities around the world to benchmark and execute their physical and e-Document ID programs, the SIA provides two online self-assessment tools that enable public bodies to benchmark and plan their current and future deployment projects against proven best practices.
Covering every aspect of the ID document lifecycle – enrolment, issuance, document design, personalization and support processes – the SIA’s eSAM and eSEC evaluation tools enable national schemes to also evaluate the physical security features of current documents, understand what’s required to build a secure eDocument, or evaluate the impact of future design changes on overall document security.
The physical ID imperative
People today live much of their social and working lives online – using a growing number of corporate and social media ‘identities’ to do so. Even in the arena of government-issued identity, the impetus for digital IDs and the evolution of online government service provision is a key driver for governments looking to harness the potential of identity-enabled eServices to extend social inclusion, welfare support, health coverage, and more. And, as we’ve seen, ensure that critical public services can still function during disruptions like the recent global health crisis.
However, the drive to digital does not eliminate the need for physical identity documents. Even Estonia, one of the most connected and digitalized countries in the world, still deems the physical credential as necessary. With good reason.
The continuing need for physical credentials
A government-issued legal and trusted identity enables public officials and third parties to verify, with a high degree of confidence, that we are who we say we are. This ‘token’ of government-issued identity could be a physical document like a driver licence or identity card; a physical document with a digital chip (often called an eDocument); a mobile ID (where the ID ideally should be held in an embedded secure element in a smartphone to achieve a high level of end-to-end security); or a digital ID that exists online and has no physical presence.
Examples of hybrid solutions, known as phygital ID (which blends digital and physical interactions to provide right time, right place interactions), are also emerging on the market and should be absolutely considered in the near future.
The choice of token, and all associated levels of document security and privacy protection, is determined by appropriateness and proportionality to the scenario. In other words, governments need a token that allows individuals to prove their identity, and have it verified, in multiple scenarios. Which is why physical documents – and more particularly, physical eDocuments – continue to be so relevant.
Last but not least, physical documents provide an essential lifeline to social welfare payments for hundreds of millions of people around the world. They also represent a powerful emotional connection to a region or state, and a sense of identity that transcends the actual use case of the document.
Identity is, at its heart, a people-centric issue and the importance of this should not be underestimated, whatever road governments choose to travel.
Verifying identity in both digital and physical spaces
Physical ID documents are a practical necessity in any given offline environment – be it remote or rural locations without internet connectivity, or even in metropolitan areas where coverage is patchy. Added to which, smartphones run out of battery – and not everyone has a smartphone. Which is why Mobile ID is best employed as a companion service to the physical document.
To secure borders, make their roads safer and reduce fraud, many governments around the globe are now making significant long term investments into eDocument programs that provide a convenient bridge to the online world. In a traffic stop scenario, for example, if a police officer’s reader is connected to the internet, anti-fraud checks and background checks can be conducted automatically.
With citizen usage of mobile ID growing around the globe, deploying a Public Key Infrastructure (PKI) applet into the chip will futureproof the eDocument – allowing it to be used to securely access online government services. Far from being outdated and irrelevant, physical eDocuments are not only vital in proving identity in any given offline environment, they are also the foundation for doing the same in the digital world too.
The critical role of security
The evolution of document security
It would also be wrong to assume that physical documents don’t offer the required levels of security when crossing borders or dealing with government agencies and law enforcement. This is an important consideration in an era when widespread access to low cost technologies - including high quality scanning, color copying, image processing and photo quality printing – means the capacity of individuals to produce convincing counterfeit travel documents and very deceptive alterations has increased significantly.
A wide variety of techniques can be utilized to strengthen the security of a wide range of physical documents and improve their resistance to attack and misuse. These include the use of ultra-fine resolution printing and watermarks that are incorporated into the document during production, or features that change a document’s appearance when viewed in different lighting or observation conditions.
Some features and solutions that protect against current attacks by counterfeiters and fraudsters can be weakened over a relative short period of time (2-3 years). For example, high-resolution scanning and printing equipment, and some basic security inks, have become available to the general public. Even laser engraving equipment is no longer exclusive.
Authorities are able to implement automated inspection techniques of documents. For example, image analysis combined with biometry allows high level comparison of the face of the holder of the document with the printed photo while the MRZ (machine readable zone) can be used to easily capture personalisation data. Not only does this verify the authenticity of the document, it verifies the owner as well.
eDocuments take this analysis further. The onboard chip contains personal data that can be read and compared with the physical information printed on the card (to ensure authenticity) and with the user (to ensure they are who they say they are). This on-card matching can be conducted in any offline scenario using a handheld reader.
The need for Document security
There are many ways in which the integrity of a secure identity document and the process used to create it may be attacked. For both machine readable official travel documents (MRTD) and eMRTDs such as passports or visas – or emergency documents that may utilize a visible digital seal rather than a chip - these can include:
• Forgery—a genuine passport altered to show a different holder’s name and/or facial image, change dates or where the biodata page or visa has been changed (for example, to a counterfeit replacement)
• Counterfeit—a false document manufactured as such
• Theft of components, materials or blank documents to be used in forgery or counterfeiting
• Lookalike passenger—for example, using a lost, stolen or borrowed passport
• Fraudulent application—Fraudulently Obtained Genuine (FOG), or the utilization of a ‘morphed’ passport photo that digitally blends the facial features of the fraudster with those of the original carrier’s image.
ID document forgery is constantly evolving, and methods now include placing an overlay with portrait image and personal data on top of the data page, grinding away the back of the PC data page to access the personalized layer, or adding laser engraved personalization.
Defining eDocument security at every stage of the process
Protecting the integrity of a critical document such as a passport or ID card requires a 360-degree rigorous end-to-end approach to all aspects of security that must include:
• all stages of production
• the transportation of documents and all component parts and materials used in production
• the storage of blank documents awaiting personalization
• the application process for someone requesting any of these documents.
To ensure optimized sustainability of new ID documents, authorities must focus on the initial design process. The first task is to analyse all the potential threats (which documents are frequently reproduced or altered; what techniques are used by forgers).
Since it is vital to make it extremely difficult to both reproduce the document and change the data on the document, the features selected in the design process must protect against all types of threats (copying, reproducing, data alteration or attempts to personalize a blank document).
Some essential security safeguards for document design include:
• using visible security feature technologies that are difficult to reproduce but also to simulate – this may include laser engraving, combining several optical elements, sealer technology that embeds a transparent color-shifting strip or patch into the credentials
• combining security features that make it more difficult for a counterfeiter to master all the various techniques necessary to properly copy or alter a genuine ID document
• combining tactile (feel) and optical (look) features
• using Optical Variable features – such as 3D holograms, images that are only visible under UV light or optical variable ink that changes color depending on the light used to look at it
• preventing direct access to personal data by inserting these inside the document structure, or by adding an overlay protection or watermarks that make it difficult for fraudsters to replace the data page
• integrating and interlocking personal data and security features – for example, using anti scan patterns, or adding laser engraved information or embossing after personalization has taken place
• duplicating personal data, using various techniques, including laser etching the edge of documents with the holder’s personal information (name, serial number or other unique information).
Security: from design to manufacturing, distribution, issuance and verification
As we’ve seen, issuing authorities will need to enable a number of structural security features to minimize the risk of falsification, alteration, deconstruction or tampering. They will also need to consider every aspect of the document lifecycle process to ensure they can issue and authenticate documents with confidence – this will include defining the right materials (parts), the unique processes and product construction and level of durability required.
The four pillars of eDocument security
• Strict control over security at all stages of production, including component parts and materials, transport and storage, and printing, personalization and issuance to the applicant / holder.
• Secure design, production and personalization to make copying or amendment as hard, and as obvious, as possible.
• Secure electronic chip—containing data on the passport and holder with high security, cryptographic-based digital signatures to authenticate the source, data and the chip itself.
• Inspection – though taking place later, good awareness of security features so inspection of documents and persons presenting them at the border is as effective as possible.
At the design stage, consideration should be given to every component of the document – this includes the physical and security features, unique numbering and materials that will be incorporated, the printing and anti-copying techniques and elements that will be utilized, the document’s design (especially the data pages), and which embedded chip, operating system and protection mechanisms will be utilized.
Next the manufacturing process for every component needs to be assessed – from production in a secure facility to the way/point/location at which personalization features/data are incorporated. Ensuring each component is manufactured to the required security level requires a level of investment that should not be bypassed.
Decisions will also need to be taken about whether to pursue a centralized or decentralized production and distribution. In other words whether blank documents (the base stock) will be tracked and sent to personalization centers in readiness for issuance or stock will be securely managed centrally. Detailed risk analysis needs to be applied to both scenarios (sometimes, both approaches will run in concert) to establish the potential vulnerabilities).
Next, issuing authorities need to be confident they have the appropriate enrolment and registration systems and processes in place to ensure that personalized ID is issued to the right owner and are able to verify that an individual’s claim to the ID is valid.
The security process does not end at distribution stage. Once a secure document is issued to a citizen, it is no longer under the control of the issuing authority. Indeed, rigorous and skilled inspection are required when any such document is presented for inspection at the border. This is needed to protect against the use of lost or stolen documents, use by a lookalike passenger (an imposter), use of a fraudulently obtained passport, or the arrival of someone of interest to the authorities—for example someone wanted by the police.
Free online evaluation tool from the SIA
Supporting the evolution of eDocuments
To support governments in the development of their eDocument programs, the not-for-profit Secure Identity Alliance has developed the eDocument Scheme for Evaluating physical seCurity (eSEC) Webtool. This tool is available online and is free to use by public bodies and agencies.
Providing a method to benchmark and evaluate the security aspects of the design and issuance elements of their eDocument programs, the tools can be used to generate a global benchmark score of each step of the program, together with detailed recommendations on how to improve program security.
Providing a much-needed ‘common criteria’ approach to the development of security features for passports, identity cards, driving licenses and similar identity-based eDocuments, these web-based tools offer a convenient and simple self-assessment approach to assess the robustness of their programs. Uniquely, these tools also make it possible for governments to evaluate the best balance between security, cost and convenience for every individual eDocument program, and how well different security feature levels are distributed within each document.
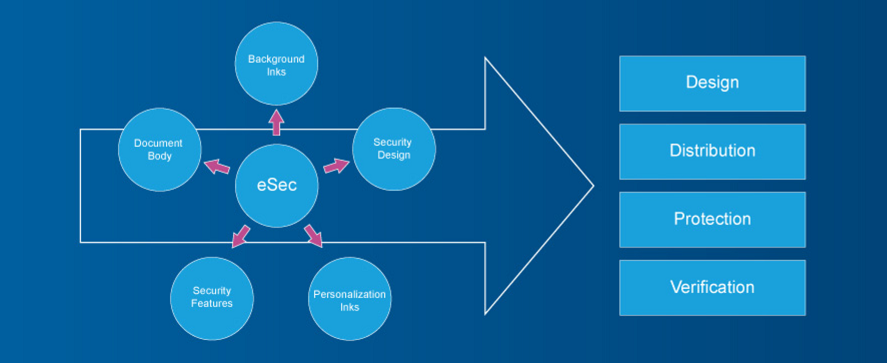
eSecurity Evaluation Model (eSEC)
Developed by the SIA, the eSEC model supports the evaluation of the physical security features in an eDocument. Organizations can select the document type, list the security features of a current or planned document, and answer questions about the design process.
The tool provides a benchmarking score for known strengths and the ability of a document to counter potential threats is then provided. Different protection profiles can be set so that products can be evaluated against a variety of potential security threats, the combined security strength of documents can be verified, and potential again and wear on security features evaluated and tested.
For organizations that face dealing with multiple security features and technologies, the eSEC tool offers a highly effective way to compare document security levels against measurable global benchmarks.
Conclusion
As we’ve seen, physical ID documents will continue to play a key role as a token of government-issued identity for the foreseeable future. But as governments evolve their identity schemes to bridge the physical and digital worlds, and evolve their delivery of digital citizen services, the prevalence of e- and 'phygital' documents is set to increase.
The recent global health crisis means many governments are now set to accelerate their eID programs in a bid to ensure social protections and enable everyday public service interactions for citizens. Or leverage trusted government-derived digital identity services to respond more effectively – and recover faster – from unforeseen disruptions that impact the population.
Providing an ideal way to enable the growing numbers of citizens who are willing and able to embrace mobile ID, assuring the security of eDocuments in both the physical and digital realms is paramount. To this end, the Secure Identity Alliance has created two powerful tools to support governments and issuers to evaluate their current and planned eDocument physical security design features.
With governments around the world investing in ultra-secure identity credentials for citizens, understanding how resistant to attack these documents are, whether they are cost effective, and if the security measures selected will remain viable for the lifetime of the document has never been more critical.