Making Secure Electronic Documents Cyber Resilient

Imagine being denied entry to a foreign country because the electronic chip in your travel document is considered vulnerable and you would have to request a visa before traveling there? Because travel documents usually have a 10-year validity, this is a valid concern and is the reason why we consider micro-controllers (often called chips) in secure documents to be high value components.
As one of the most basic instances of the advanced IT solutions available in the industry, secure software embedded in ePassports and keeping them safe from their Cyberattacks are the object of deep concern and attention, especially with the increased adoption of digital ID, often derived from a secure electronic document such as a passport.
Cybersecurity is an ever-evolving concern. Setting up a secure identity document project relying on highly certified products is a necessary practice but not sufficient for protecting identities from future Cyberattacks. Active monitoring and anticipation of Cyber threats is critical to protect sensitive assets. Such threats include eavesdropping, cloning, or extracting highly confidential fingerprints from the electronic chip.
Decades of security progress have been framing an always-improving environment focused on a single objective: defining and maintaining a Cybersecurity framework to deploy secure embedded solutions in electronic ID documents.
The next step is to look beyond Cybersecurity and focus on Cyber resilience, which refers to an entity's ability to continuously deliver protection, despite adverse events. This combines information security, business continuity, and organizational resilience. This is particularly relevant for governmental programs, who should continue to issue secure identity documents to their citizens at any point in time.
Concretely, the future Cybersecurity of ID documents like ePassports depends on the ability to update, in the field, the secure embedded software (for example algorithms used for the various security mechanisms) protecting the data stored in the chip – with no need to issue a new document.
How does Cybersecurity work in an ePassport scheme?
The ePassport features a micro-controller with specific secure embedded software. The role of such software is to securely manage the storage in the electronic chip of personal information related to the holder, along with additional biometric data and issuing country specific data. The software provides the required authentication keys and algorithms to communicate with the inspection system, using contactless interface and standard ISO commands, formatted in an interoperable way (as specified by ICAO 9303) so that it can be used at any inspection system in the world.
Security mechanisms are evaluated according to a security certification scheme to guarantee their strength.
The cryptographic protocols implemented in the ePassport provide specially designed, state of the art protection of the electronic document and the personal data (including biometrics) it holds, that has undergone a thorough reviewing and certification process by academics, national security agencies and the industry. As security is a permanent race against fraud, active monitoring of today’s threats is critical to protect sensitive assets, but also anticipate the protections for the future.
The main security attributes include:
- Authenticity of the document: proof that the document is genuine. Protects against forgery.
- Authenticity of the data: proof that the personal data stored has not been altered after issuance (authenticates the issuing authority, also called the document signer).
- Authenticity of the roles: mutual authentication of parties involved in the transactions (passport holder, inspection system, passport document) guarantee segregated access control to the personal data and prevent illegal access.
- Confidentiality, integrity: data exchanges between the ePassport and the inspection system are protected in both integrity and confidentiality. This is referred to as secure messaging.
- Privacy: those mechanisms work together to protect the personal data and are hence not only security, but also privacy-enabling, features. In addition, the cryptographic protocols have been designed in such a way that data access requires user consent and issuing authority access right granting. In particular, this provides built-in protection against eavesdropping. Privacy is achieved through several standardized security mechanisms.
The mechanisms ensure that the micro-controller is genuine and that the data stored in it has been signed by a valid issuing authority. Underlying algorithms, with different key lengths, are used to execute the cryptographic calculations that are necessary to those mechanisms.
ICAO manages a central repository called the Public Key Directory (PKD) for exchanging the information required to authenticate ePassports. The PKD contains:
- Document Signer Certificates (DSCs)
- Certificate Revocation Lists (CRLs)
- Country Signing Certificate Authority (CSCA) Master List
Each State (country) issuing an ePassport establishes a single Country Signing Certification Authority (CSCA) as its national trust point for ePassports. CSCA certificates issue the Document Signer Certificates that are then used to create digital signatures on ePassports.The Document Signer is then checked against the CSCA to validate the digital signature. This process is illustrated in Figure 1 (below).
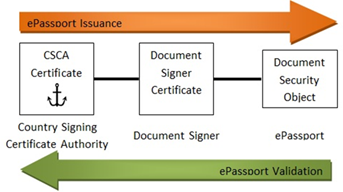
Figure 1: Process of Secure Passport Issuance & Authentication
Verification Mechanisms to Detect Potential Cyber Fraud
The table below illustrates the process by which the mechanisms are verified to detect potential fraud in case of Cyberattacks.
|
Mechanism |
Purpose |
Authentication and Verification Process |
How do we detect fraud? |
|
Passive Authentication |
Authenticity of the document Authenticity of the data Integrity |
Data groups in the micro-controller (DGs) are digitally signed by the issuing country. Signatures are stored in EF.SOD (Data Structure signed by the Document Signer) + public key (Document Signer Certificate, or DSC.). Verify signatures of DGs and EF.SOD with DSC. Verify signature of DSC with issuing authority Country Signer Certificate (CSC) from ICAO PKD. |
Invalid signature of data on micro-controller Invalid or missing certificate chain to issuing authority |
|
Basic Access Control |
Confidentiality Privacy |
Machine Readable Zone (MRZ) shall be visually read from the passport to calculate access key. This key shall be used to grant access to the micro-controller using symmetric authentication (based in 3DES, a symmetric-key block cipher). Symmetric session keys are exchanged and used to encrypt the communications (secure messaging) |
MRZ often improperly formatted, so micro-controller does not read it. |
|
Supplemental Access Control |
Confidentiality Privacy |
MRZ or CAN (Card Access Number) shall be visually read from the passport to calculate access key. Use asymmetric Diffie-Hellman (mathematical method of securely exchanging cryptographic keys over a public channel) key exchange with micro-controller based on mapping functions defined in EF.CardAccess (a file required for the Password Authenticated Connection Establishment mechanism.) Elliptic Curve and traditional Diffie-Hellman algorithms are supported. The key exchange generates a set of strong AES (Advanced Encryption Standard) or 3DES sessions keys used for secure messaging. |
MRZ or CAN often improperly formatted, so micro-controller does not read |
|
Active Authentication |
Authenticity of the document |
Readable data contains a public key (DG15) and corresponding private key is stored in the micro-controller in a secure area. The micro-controller signs a random piece of data with the secure private key. The signature is verified with the public key. Passive Authentication is required to ensure integrity of the public key in DG15 |
Micro-controller may be cloned or copied, so signature verification fails |
|
Chip Authentication |
Authenticity of the roles Confidentiality Privacy |
Readable data contains public key info (DG14) and corresponding private key is stored in the micro-controller in a secure area Use asymmetric Diffie-Hellman key exchange with micro-controller. Elliptic Curve and traditional Diffie-Hellman algorithms are supported. The key exchange generates a set of strong AES (or 3DES) sessions keys used for secure messaging. |
Micro-controller may be cloned or copied, so signature verification fails |
|
Terminal Authentication |
Authenticity of the roles Confidentiality Privacy |
Readable data contains a CVCA (Country Verifier Certification Authority) reference in EF.CVCA (a file containing the public key of the certification authority) to a CV certificate chain used to verify the terminal. Micro-controller stores a trust point with the CVCA root certificate for the certificate chain, which includes permissions on micro-controller data. Micro-controller verifies the CV certificate chain and permissions provided by the terminal. CV, DV and IS certificates. Terminal signs a challenge from the micro-controller with the IS private key stored in a secure area locally or remotely. Terminal verifies the challenge to ensure authenticity of the terminal IS (Inspection System) private key. |
Allows micro-controller to verify terminal access rights to data. |
The Role of Common Criteria Certification
Multiple security frameworks can be used when evaluating the security of an ePassport secure embedded software. As an example, banking cards are ruled by the EMVCo scheme (EMVCo is a global technical body, industry-wide collaboration, to facilitate the worldwide interoperability of secure payment transactions by developing and publishing the EMV® Specifications and their related testing processes. EMV stands for "Europay, Mastercard, and Visa", the three companies that created the standard).
A similar environment has been adopted as the reference for most identity documents: the Common Criteria evaluations (which was defined before EMVCo). The Common Criteria for Information Technology Security Evaluation (abbreviated as Common Criteria or CC) is an international standard (ISO/IEC 15408) for computer security certification with international and mutual recognition agreement. Over the last 25 years, CC has been the undisputed reference Cybersecurity framework for the IT and Security industries.
Common Criteria provides assurance that IT security products have been specified and evaluated in a rigorous and repeatable manner and at a level commensurate with the target environment for use.
Originally developed to unify and supersede national IT security certification schemes from several different countries, including the US, Canada, Germany, the UK, France, Australia and New Zealand, Common Criteria is now the widest available mutual recognition scheme for secure IT products and is often a pre-requisite for qualified digital signatures under the European Union digital signature laws. This applies to EU ID documents such as Passports, Identity cards, Resident Permits, Social Security cards.
The Common Criteria standard provides an assurance on different aspects of the product security covering areas such as:
- Development of the product and related functional specification, high-level design, security architecture and/or implementation design.
- Guidance of the product and related manual for the secure preparation and deployment of the product.
- Lifecycle of the product and all related processes applicable during its creation such as configuration management or secure development process and tools used to the deployment and retirement of the product with the lifecycle design and delivery process.
- Supporting security policy documentation.
- Tests of the product and particularly coverage of the functional security requirement
- Vulnerability assessments
More information is available on the Common Criteria portal
Certification is performed according to specific Cybersecurity guidance tailored to the application at stake – guidance called Protection Profile (PP). The depth of the certification is ruled by a scale (Evaluation Assurance Level) ranging from 1 to 7. Evaluation is always extremely demanding in terms of Cybersecurity reliability – typically 3 months of white box penetration testing by skilled, independent evaluators. White-box testing is a method of software testing that tests internal structures or workings of an application, as opposed to its functionality (black box testing).
The security challenges attached to these evaluation schemes are extremely demanding and the state of the art is continuously evolving. The industry is also innovating, looking for new methods and new algorithms to cope with this evolution. The industry is constantly coping with this evolution, as cryptographic algorithms are also evolving. For this reason, as it comes to embedded operating systems, the evaluations eventually end-up being a superstructure made of multiple layers:
- Common criteria certification of the electronic chip, where security of the chip is assessed and aligned with the latest findings related to hardware security.
- Certification of the secure embedded software, focused on the analysis of the implementation, ensuring that it demonstrates resistance to the latest software security threats.
- Often there is a third certification, typically an application (e-Identity, e-Passport, e-Healthcare…) dealing with the software implementation of practical applicative services inside the product.
Such multi-layered certifications are commonly referred to as “composite” certifications where one can see that an ultimately challenging task in terms of security has been divided into multiple layers in order to be executed through a safe and efficient methodological approach. Such certifications are aligned with international standards to allow interoperability.
Moving toward protection that stays ahead of Cyber threats
Until recently, the Common Criteria Cybersecurity framework had not defined any coordinated approach related to the time bounding of CC certification. Cybersecurity monitoring was a recommended practice, performed by most of the key actors in the industry, but it was not always formalized administratively except by few security agencies for their national needs.
A major change occurred in July 2017, when the CCRA (International Organization of National Security bodies dealing with Common Criteria) decided that once granted, the mutual (i.e., international) recognition of a CC certificate validity will come to an end five years later. A default lifespan of 5 years has been considered a good balance between certification bodies’ requirements and business requirements. A re-assessment (surveillance or re-certification) is required before the 5 years to extend the validity of the certificate.
Among the changes in progress, the ability to update products in the field is now an option. New generations of products coming from the industry are starting to offer such “update” capabilities. Such solutions enable issuing governments to react more effectively in the case of Cyberattacks.
It is currently possible to update citizen data, like updating digital signature certificates and loading new applications on electronic identity documents. This is called a post issuance update. The novelty is that such updates focus on the secure embedded software and, as example, the cryptographic library used for the various security mechanisms.
The diagram below is a visual representation of a typical chip structure (what is inside) and illustrates which components are modified during an update like the one described above.
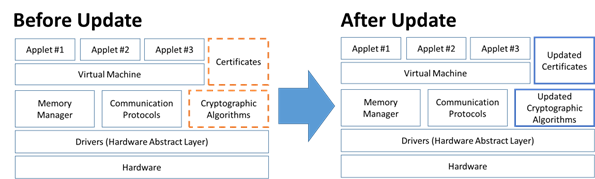
Figure 2: Before Update/After Update
There are several possible ways to update those documents. This could be when going through border control (in the country of issuance), in self-service kiosks in designated areas (airports, police stations, city halls) or even with a mobile phone using the integrated NFC reader and a dedicated app.
We believe post issuance, remote update capability for electronic identity documents is the security model for tomorrow. Just like computer or a smartphone, secure identity electronic identity document shall offer the updatability to limit the risk from cyberattacks.
Surveillance aims at extensively re-evaluating the product in its original configuration at the time of the initial certification versus up-to-date, state of the art Cybersecurity threats. The surveillance process can result in a FAIL status, voiding the certificate previously obtained. CCRA also strongly recommends that Cybersecurity products can be updated after their issuance. The upgrade will allow, for example, the disabling of an algorithm deemed weak and switch to a more secure one, without having to recall a document and issue a new one – a key benefit for authorities looking to offer their citizens secure, convenient and cost effective solutions.
Quantum computers: A future threat
We must also consider the development of Quantum computers and their potential impact on current cryptographic schemes and how vital the ability to upgrade document security in the field will be in this long transition ahead of us.
Cryptographically Relevant Quantum Computers (CRQC) are far from becoming a reality; current prototypes are far from having the required processing power and many challenges in physics, engineering and computer science must be overcome before scaling up to large quantum computers able to solve the factorization and discrete logarithm problems on which the current PKI is based. The working hypothesis that CRQC will be available in the early 2030s.
However, there is a latent threat of a “store now, decrypt later” attack. The main risks for an ePassport are deciphering issuing authority Document Signer certificates to sign a fake document and the retrieval of additional biometrics (protected by Extended Access Control mechanism).
Ideally, the migration to more robust systems should start well before the availability of CRQC so that threat timeline is as limited as possible. ICAO New Technology Working Group is following the topic closely and plans to draft a proposal for objectives and next steps in the first half of 2023.
ANSSI, the French National Agency for the Security of Information Systems, has drafted some recommendations for the transition over the next decade. Other agencies like BSI (German equivalent of the ANSSI) and the US NIST have released extensive material related to the rise of quantum threats and the recommended first steps to migration.
ANSSI recommends introducing post-quantum defense-in-depth as soon as possible for security products aimed at offering a long-lasting protection of information (until after 2030) or that will potentially still be used beyond 2030. All post-quantum PKC algorithms shall continue to be systematically included inside hybrid mechanisms. ANSSI expects that after years of analysis, the security assurance level provided by post-quantum algorithms will be as high as today’s pre-quantum assurance level. Thus, the usage of some post-quantum schemes should be possible without hybridation.
Conclusion
We hope thisarticle has given you a clear understanding of the benefits of Cyber resilient secure identity documents. Over the past few years, many governments have extended their global Cybersecurity threat assessment to also include identity documents.
The industry, including several SIA member companies, is supporting government initiatives in this area, providing expertise on the topic.
Cyber resilience of ePassports can be achieved through a thorough approach:
- Anticipate: prevent attacks as much as possible, make life difficult for hackers
- Resist: reduce the severity of the attacks
- Monitor: develop a system to track Cyberattacks
- React: manage the impact when an event does happen
- Restore: learn from the experience to improve
Security relies on expertise, anticipation, and reactiveness. Within the fast moving environment detailed in this series, it becomes obvious that only the setup of a well-structured risk management organization is the solution for an efficient handling of demanding Cybersecurity projects.
Risk management will allow to react to an event, while planned migrations over the course of the project will reduce the impact if a threat arises.
Other key elements can be considered to minimize the exposure to Cyberattacks by applying good practices already proven in the field. For example:
- Anticipation by planning regular product renewal/migrations over project life for both the secure embedded software and the issuance platform.
- An ePassport may well be modernized only when it comes to the digital configuration (chip/OS), while the physical configuration (the booklet appearance and security features) remains the same. There is no visible change for citizens between two versions (only the chip of newly issued documents is updated), but electronic security (Cyber protection of passport holder's data) is kept state-of-the-art.
- Agile design for Issuance and eDocument management solution (product change and patch deployment). Reactiveness is about detecting potential threats early on and rolling out appropriate patches to the documents in the field to reduce the exposure to the vulnerability.
- end -
This article was written by the ‘Document Security’ working group of the Secure Identity Alliance. This working group aims at “Guiding the design, manufacturing, issuance and verification of convenient and cost-effective secure documents”. Among other publications, a further note explaining more details of what is PKI (Public Key Infrastructure) and how secure ePassport chips result in trust and efficiency can be found here.
Glossary
Data Groups (DG)
A series of related data elements grouped together within the Logical Data Structure defined by ICAO 9303
EF.SOD
Data Structure signed by the Document Signer, which carries the hash values of the LDS Data Groups
EF.CardAccess
EF.CardAccess is a file that is required for the Password Authenticated Connection Establishment (PACE) mechanism, to store the security information required by the protocol.
Document Signer (DS/DSC)
The Document Signer digitally signs data to be stored on ePassports.
Country Signer Certificate (CSC)
Each State issuing an ePassport establishes a single Country Signing Certification Authority (CSCA) as its national trust point in the context of ePassports. CSCA certificates are generated and are generally used for periods of three to five years. CSCA certificates issue the Document Signer Certificates that are then used to create the digital signatures on ePassports. The Document Signer must be validated against the CSCA to validate the digital signature.
Country Verifying Certification Authority (CVCA)
The Country Verifying Certification Authority enforces the privacy policy of the issuing Country with respect to the protection of sensitive biometric reference data stored in the ePassport. The CVCA represents the country specific root of the PKI of Inspection Systems. The CVCA determines the access rights that will be granted to all Document Verifiers (DV), foreign and domestic, and issues certificates containing the individual authorizations to each of those DVs.
Document Verifier (DV) Certificates
The DV enforces the privacy policy of the receiving Country with respect to the protection of sensitive biometric reference data to be handled by the Extended Inspection Systems. The DV manages the authorization of the Extended Inspection Systems for the sensitive data of the ePassport in the limits provided by the Issuing State. The DV manages a group of terminals (e.g. terminals operated by a State’s border police) and issues authorization certificates to those terminals. A DV must have already received an authorization certificate from the responsible CVCA before it can issue associated certificates to its terminals.
IS (Inspection System) Certificates
Inspection Systems used for inspecting ePassports, usually at border control, require specific certificates for accessing restricted areas of the memory (additional biometrics) and require a valid certificate to perform mutual authentication.
Machine Readable Zone (MRZ)
Fixed dimensional area located on the front of the passport data page containing mandatory and optional data for machine reading using OCR methods
Card Access Number (CAN)
The CAN is a number printed on the document and chosen randomly. In contrast to the MRZ, the CAN has the advantage that it can easily be typed in manually. It helps to establish a session key with the secure embedded software.
3DES
Triple DES is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block.
Diffie-Hellman
Diffie–Hellman is a mathematical method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols
Elliptic Curve Cryptography (ECC)
ECC is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys compared to non-EC cryptography to provide equivalent security.
Advanced Encryption Standard (AES)
AES is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST)

